| 编辑推荐: |
本文来自于www.8btc.com,在本文中,我们将对两个
payload 进行分析研究,这两个恶意程序之间是相互配合的,一个被称为 Upatre(负责下载其他恶意程序),一个被称为Dyreza(负责窃取用户各类身份信息)。
|
|

在过去一段时间里面,我们分析了Dyreza的核心代码以及使用的技术,那接下来我们将逐步对其进行解析。
什么是Dyreza?
Dyreza,其目的是窃取银行账号和比特币。整个流程首先是通过Upatre进行Dyreza的下载,据研究,目前提供Dyreza下载的服务器均为路由器(大部分为AirOS和MicroTik)。而攻击者利用入侵的路由器,存在多种加密的资源包,而受到感染的机器,会通过Upatre下载路由器中存放的加密恶意代码程序,然后在用户系统中进行解密后得到Dyreza木马。
我们要对其进行分析的意义在于,恶意程序Dyreza家族目前存在有许多的变种,但是他们的主要行为轨迹还是存在共性的。我们通过分析其特性及共性,能更好地进行防御。
0×00 样本分析
-----
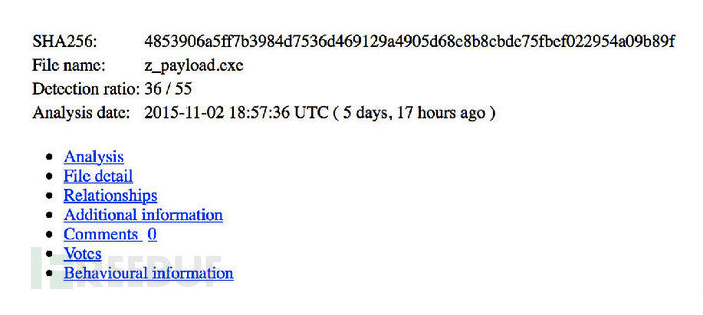
样本:ff3d706015b7b142ee0a8f0ad7ea2911
Dyreza 的可执行文件,一个僵尸网络的客户端,负责执行主要的恶意操作。
-----
-----
样本:
5a0e393031eb2accc914c1c832993d0b – Dyreza DLL (32bit)
91b62d1380b73baea53a50d02c88a5c6 – Dyreza DLL (64bit)
-----
0×01行为分析
当 Dyreza开始感染计算机的时候,它拥有较快的扩散感染速度。我们可以通过在进程管理中查看到它,同时最直观的一点,可以发现许多新的进程被创建接着又结束,像explorer,
svchost, taskeng等进程,而所进行的这一阶段,就是为了混淆其执行的流程,干扰安全人员的研究和分析。
接下来,它将两个通过正则表达式 [a-zA-Z]{15}.exe , i.e vfHNLkMCYaxBGFy.exe以伪随机码命名的恶意程序复制文件放进C:\Windows以及%APPDATA%目录下,然后通过在任务调度中添加一个新的任务,在每分钟不断地执行恶意程序样本,确保恶意程序持续执行。
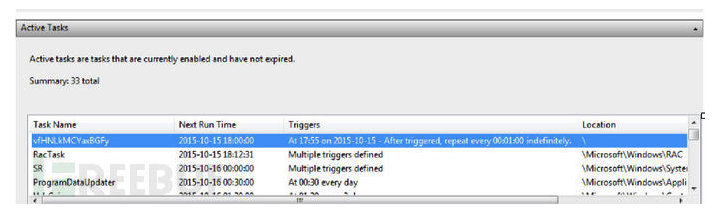
接着通过将恶意代码注入到其他进程(如svchost, explorer),然后与外界的C&C服务器进行通讯。
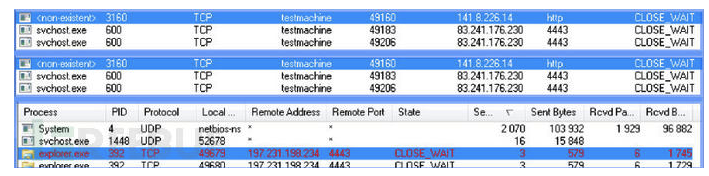
从以上观察到的结果,我们可以在 VirusTotal上查询到,上述与svchost,和explorer进程进行通讯的服务地址,其实早已经被进行标记为恶意地址了,主要的结果如下,
141.8.226.14 -> virustotal/141.8.226.14/information
83.241.176.230 ->
virustotal/83.241.176.230/information
197.231.198.234 -> virustotal/197.231.198.234/information/
而当安装任意web浏览器时,它也会直接将恶意代码注入到浏览器的进程中去,然后进行非法外联。这是该恶意程序与外部C&C服务器保持连接的方式,同时也执行着监控用户活动以及窃取各类身份凭证信息的功能。
通过研究也可以发现,Dyreza在将获取到的信息发送给 C&C服务器之前,会将信息作为一个小型数据库存放在名为
TEMP的文件夹中。
0×02 代码分析
环境检测
1、执行前的检测-Dyreza如果检测到机器上的 cpu数量少于2个,它将不会运行。该技术是为了进行自我保护,确保自身程序不是运行在虚拟机环境上。因为从目前的市场及设备配置的情况来看,除了虚拟机经常使用单核cpu之外,一般物理机都是双核以上的,而Dyreza也是基于这一点作为判断依据的。Dyreza是通过检测进程环境块下的线程信息块中的FS:[0x30]区域的信息来进行判断。而只有确认cpu数量满足大于2个(包括2个)之后,恶意程序才会继续执行。
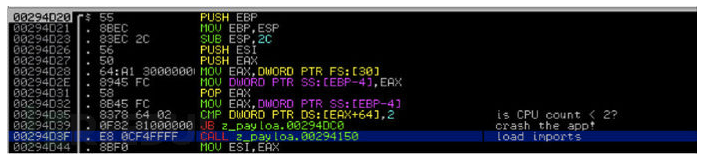
2、在执行开始的时候,恶意软件加载额外的表单到一个新分配的内存页。在运行的过程中,模块名和函数开始被解密。
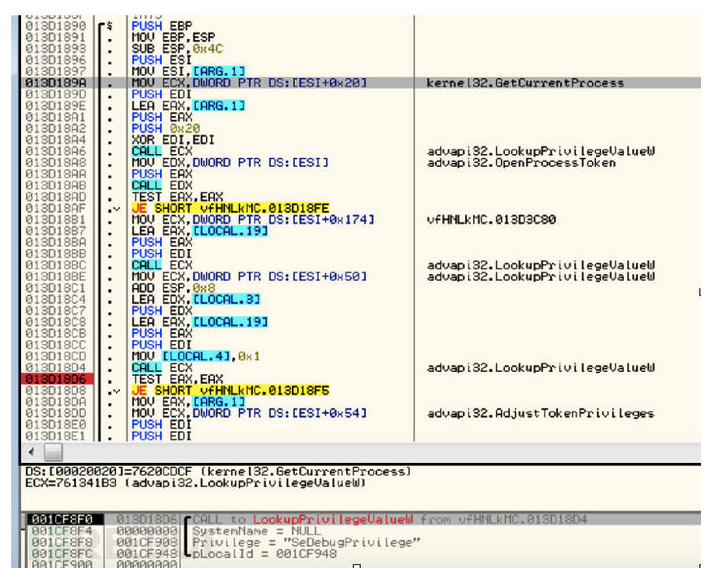
3、执行环境的检测-通过LookupPrivilegeValue函数中的SeDebugPrivilege
参数,来判断是否在调试器下进行安装,如果检测到返回值为非零值,恶意程序的执行将终止。
4、进行有效执行通过如下几个检测方式。一开始,根据初始的环境,通过对路径进行跟踪检测,如当程序运行时可执行的路径和参数。当它第一次安装时,它将会对自身进行复制,并将复制的文件放至
C:\Windows以及%APPDATA% 目录下,并将复制的程序作为一个新的进程执行安装。如果它被部署到有效路径和初始参数并通过了验证,则执行下一步检查-确认是否是第一次安装。该步骤是通过创建一个特定的全局互斥量(名称为计算机名和系统版本的哈希值,通过
GetComputerName, RtlGetVersion两个函数获取)来实现的。
5、如果这个条件满足,而互斥量也已经存在,那么它接下来将进行最重要的一步,执行恶意代码。一开始,会将加密的数据和密钥从可执行的资源包中加载。
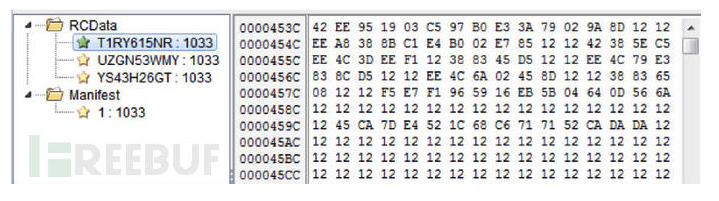
如上图,T1RY615NR-加密的32位代码,YS45H26GT -加密的64位代码,UZGN53WMY-密钥
接下来是解包,将代码取出:
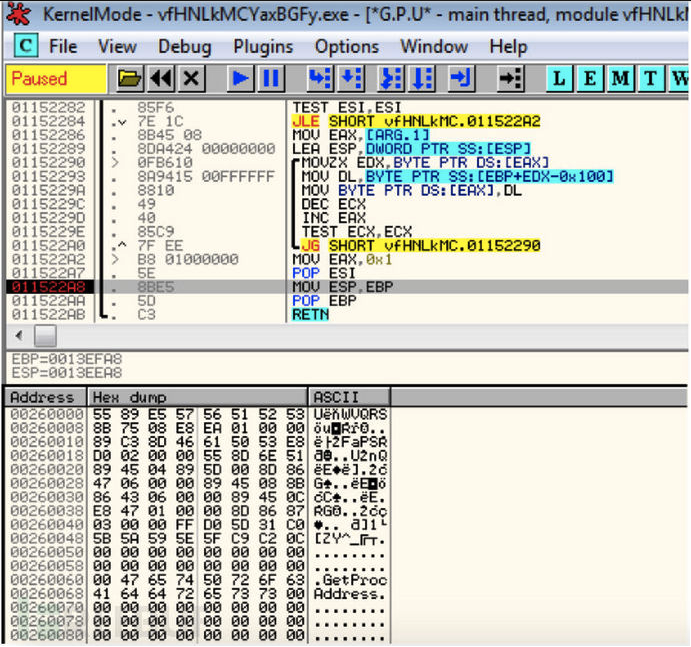
解包的算法也很简单,key_data中包含了数值和数据-在key_data中数值的索引列表。我们通过相应的索引列表来读取相应的数值。相应的代码如下,
def decode(data,
key_data):
decoded = bytearray()
for i in range(0, len(data)):
val_index = data[i]
decoded.append(key_data[val_index])
return decoded |
解密执行部分代码如下,
import argparse
import hashlib
from Crypto.Cipher import AES
BS = 16
pad = lambda s: s + (BS - len(s) % BS) * chr(BS
- len(s) % BS)
unpad = lambda s : s[:-ord(s[len(s)-1:])]
def aes_decrypt(enc, iv, key):
cipher = AES.new(key, AES.MODE_CBC, iv )
return unpad(cipher.decrypt(enc)) |
详细执行代码,可参考 dyrezadll_decoder.py
解密出来的文件包括了一个用于注入的shellcode和一个用于调用恶意程序函数的DLL(兼容32/64位)。
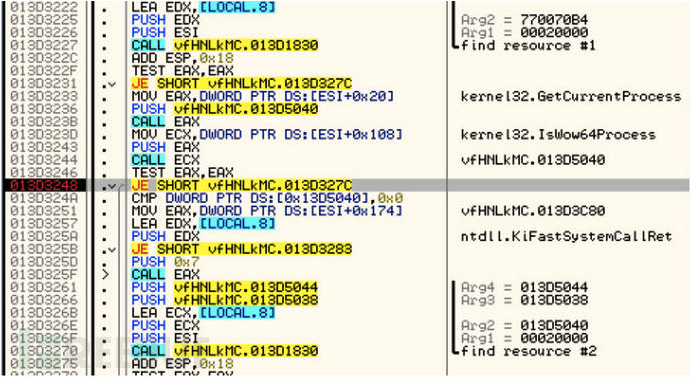
0×03 核心恶意 DLL
在这个阶段,恶意软件的功能变得非常清晰。dll文件不包含太多混淆信息–它具有明显的字符串和一个典型的导入表。
我们可以看到被用于与 C&C服务器进行通讯的字符串。
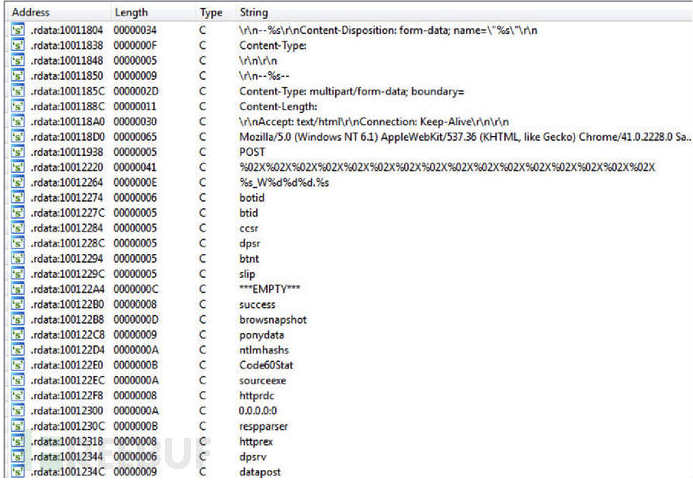
32和64位的DLL都具有相似的功能。两者之前只有架构相关部分和字符串是不同的。而通过客户端可以对系统进行识别,然后将信息发送到
C&C服务器上。
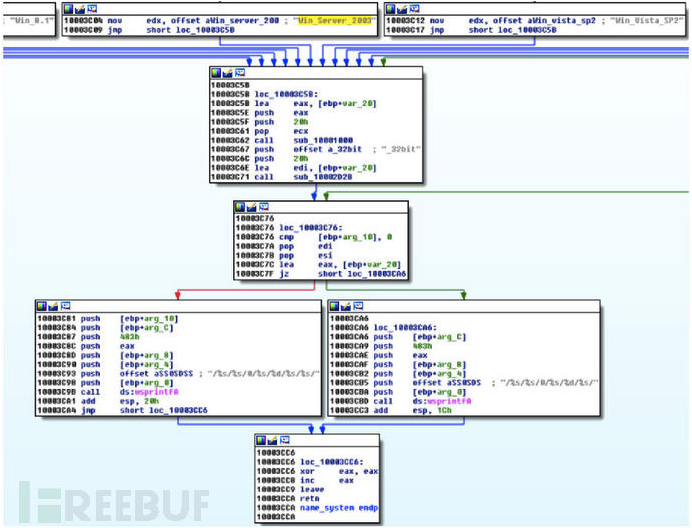
类似的程序在64位版本的DLL,只有在其硬编码字符串上用“_64bit”代替了“_32bit”:
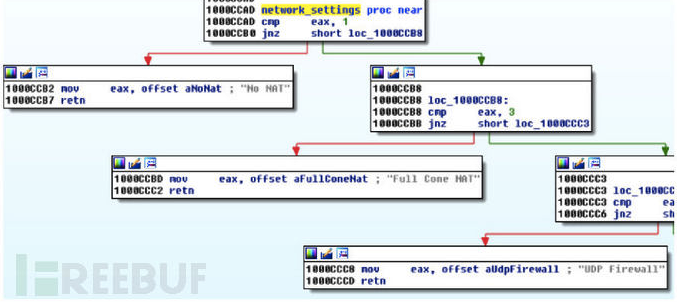
同时,对网络设置进行检查(确认并告知与C&C客户端是否可以建立后连接–命令:autobackconn)
将恶意模块注入到浏览器中执行代码:
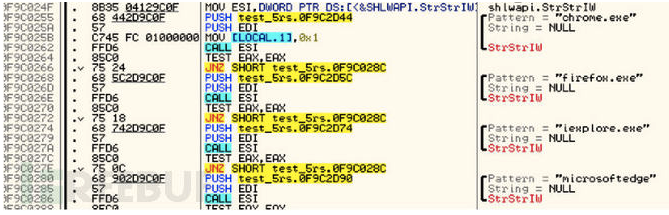
接下来,尝试发送窃取的账户信息。
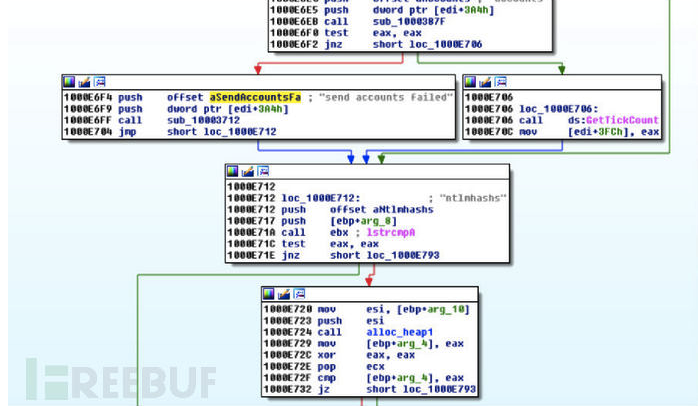
此外除了监测浏览器外,它也收集计算机上相应的基本信息(比如配置,存在用户等)
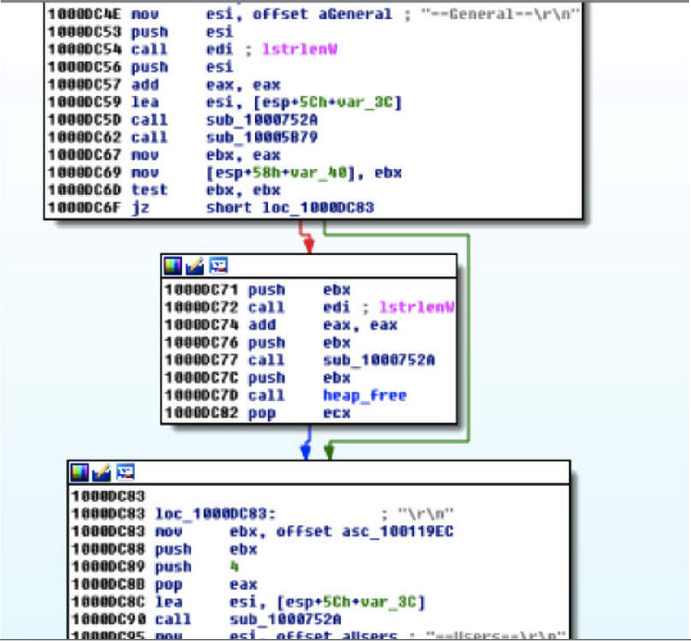
该恶意软件不仅窃取信息和嗅探用户的浏览活动,并且还试图对系统进行完全控制,目的是执行各种shell命令,如进行系统关机等,部分例子如下:
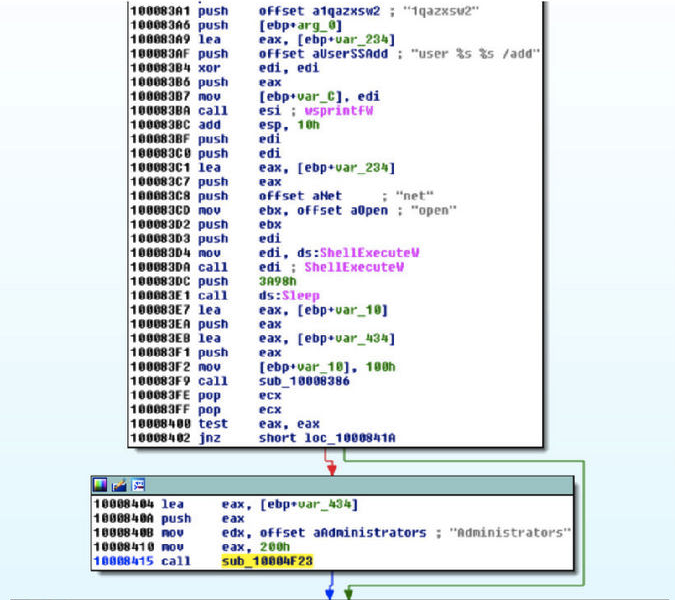
尝试创建具备管理员权限的新用户:
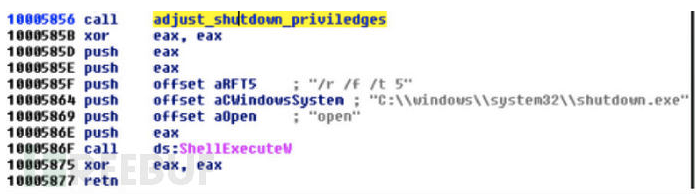
可通过命令AUTOKILLOS来进行关机操作。
0×04 C&Cs
该僵尸网络为了防止被检测到,服务器与客户端之间的通信是采用加密的方式,并采取了许多策略。
首先,C&C服务器的地址是随机从硬编码池里面挑选的。该地址池是存储在Dyreza DLL(通过AES加密算法进行加密的)的资源包中。接下来,在执行payload的时候,我们可以看到它是如何进行解密的。
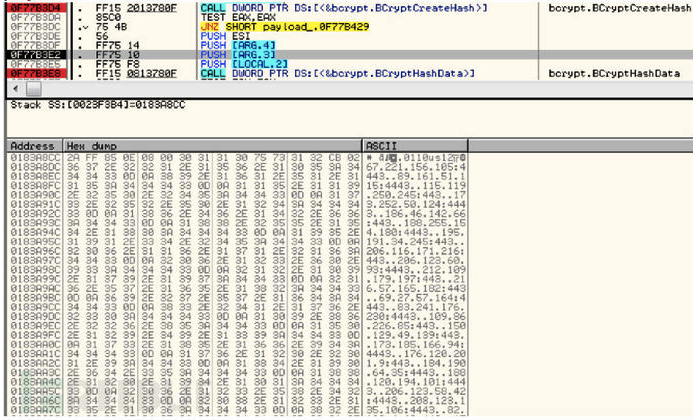
以上,是本次的分析研究探讨,具体的Dyreza代码,可以在dyreza中获取。
|